When looking for a Linux distribution for learners or students, a broad spectrum of determinants is considered. These include user-friendliness, stability, customization, and the availability of pre-installed applications to help them get off the ground with ease.
In this guide, we examine some of the top Linux distributions that streamline the learning process for students learning Linux.
1. Linux Mint
Linux Mint is a Debian and Ubuntu-based Linux distro that is among one of the most recommended distributions for learners. It provides a very simple and elegant UI that is intuitive and easy to use for newbies.
It provides 3 desktop environments for download namely Cinnamon, MATE, and XFCE. All the editions come with a pre-installed software manager that categorizes applications and makes it easy for users to easily find their desired applications.

The UI, in many ways, bears a striking resemblance to Windows XP or Windows 7 and if you are coming from a Windows environment, Linux Mint is an ideal choice.
Another attribute that makes Mint Linux ideal for students is that it bundles with a variety of free and open source applications that learners might require out of the box. These include LibreOffice Suite, Mozilla Firefox browser, VLC media player, GIMP, and on goes the list.
2. Zorin Linux
Inspired by Ubuntu, Zorin OS is yet another ideal Linux distro for students. It is an alternative to macOS and Windows designed to provide a smooth user experience for beginners and students, while at the same time granting your privacy and superb performance.
Just like Linux, Zorin provides a user-friendly UI that resembles that of Windows so you don’t need to scratch your head wondering how to get started.
Zorin provides lots of customization options with the Zorin Appearance App that lets you tweak the desktop layout to your preferred layout. For instance, you can customize your desktop to look like Windows 11, macOS, or another desktop layout that you might be comfortable with.
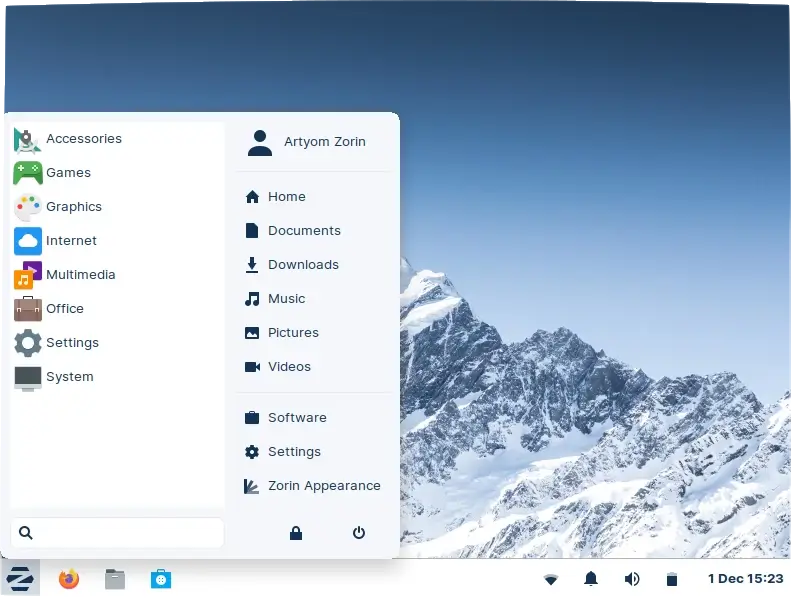
Out of the box, learners also get essential applications such as LibreOffice suite, Mozilla Firefox, and Thunderbird email client among many others.
Another reason why students should consider Zorin is its superb performance and speed which helps increase their productivity. Further, the Zorin Lite Edition is designed for older PCs, and therefore pupils can revive their old PCs and save money as they learn Linux.
3. Academix GNU
AcademiX GNU is a Debian-based Linux distribution developed specifically for educational purposes. It is built on Debian Stretch and Buster and ships with free programs for all levels of education – from primary to upper and/or university levels.
Academix GNU provides an installation utility that can be used to install a wide array of applications for topics such as Mathematics, Biology, Chemistry, Geography, Statistics, Robotics, and programming. All the applications ship with virtual interactive labs.

There’s a special section dedicated to instructors or teachers that allows them to curate articles for students and also for online publishing. Most of the educational programs or applications are licensed under the GNU GPL or BSD licenses. This distribution can be installed on a PC or run as a live medium.
4. UberMix
UberMix is a Linux distribution based on Ubuntu that is specially built with the needs of learners in mind. It streamlines the learning process for students by providing an ideal mix of preinstalled applications for learning and creativity purposes, all of which can be installed with a simple click of a mouse button.
In addition, UberMix provides a variety of IDEs providing you with the flexibility to write code in your preferred code editor. Ubermix is easy to install and you can easily deploy it in an educational institution without much of a hassle.
5. Elementary OS
Aside from its polished and elegant look, Elementary OS is a Linux distribution based on Ubuntu that is designed to help learners easily transition to a Linux environment.
Elementary OS is considered a perfect replacement for macOS and Windows, and rightfully so given the intuitive and easy-to-use UI. Users can easily launch applications from the top-left corner of the screen or from the dock located at the bottom of the screen.
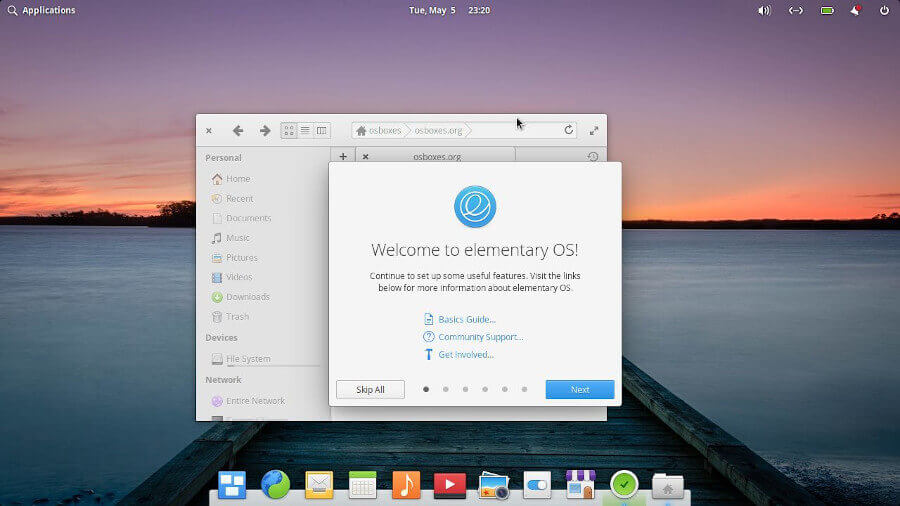
Out of the box, you get a load of applications for everyday use such as a music player, photo manager, mail client, text editor, and many others.
Elementary also provides an App Store called App Center from where you can get free and paid Apps. Each application has been carefully reviewed and developers to ensure a secure and privacy-respecting experience.
6. Ubuntu
Ubuntu hardly needs any introduction. It’s one of the most popular and widely used Linux distributions on which previously-mentioned distributions and many others have been based. Ubuntu is inspired by Debian and features a solid LTS release cycle implying that it receives features and updates at fixed time intervals.
One of the aspects of Ubuntu that stands out is its desktop which, by default, features the GNOME desktop environment which is beginner-friendly, intuitive, and requires little effort to navigate.
Ubuntu also comes with pre-installed applications such as LibreOffice suite, VLC media player, Firefox web browser, document viewer and scanner, and a host of other productivity applications to enable learners to get off the ground without a hitch.
In addition, Ubuntu provides GNOME Software, a graphical front-end for managing software packages that took over from Ubuntu Software Center. The software Center provides an easier way of managing packages for students who are not yet confident in working on the command line.
Ubuntu also offers wide online community support that provides solutions to common technical issues that learners might experience from time to time.
7. Manjaro Linux
Arch Linux is often considered intimidating especially for beginners and learners. It requires an intermediate to advanced level of working on the command line to set everything from the ground up. This is where Manjaro Linux comes in.
Based on ArchLinux, Manjaro Linux is a desktop-oriented Linux distribution that focuses on user-friendliness and provides a smooth Arch Linux experience for learners. It provides a range of desktop environments to choose from including GNOME, Budgie, Cinnamon, and MATE to mention a few.

In addition, it offers a wide range of customization options, and learners can customize virtually anything; from themes, and widgets to widgets and icons.
8. OpenSUSE Leap
OpenSUSE is another great choice for learners. It comes in two flavors – TumbleWeed which is a rolling release and Leap which is more stable and suitable for students.
An aspect that stands out about OpenSUSE is the presence of Yast (Yet Another Setup Tool). This is a front-end setup and configuration tool that performs a myriad of tasks including hardware configuration, firewall, and network management, enabling and disabling system services, software updates, package management and so much more.
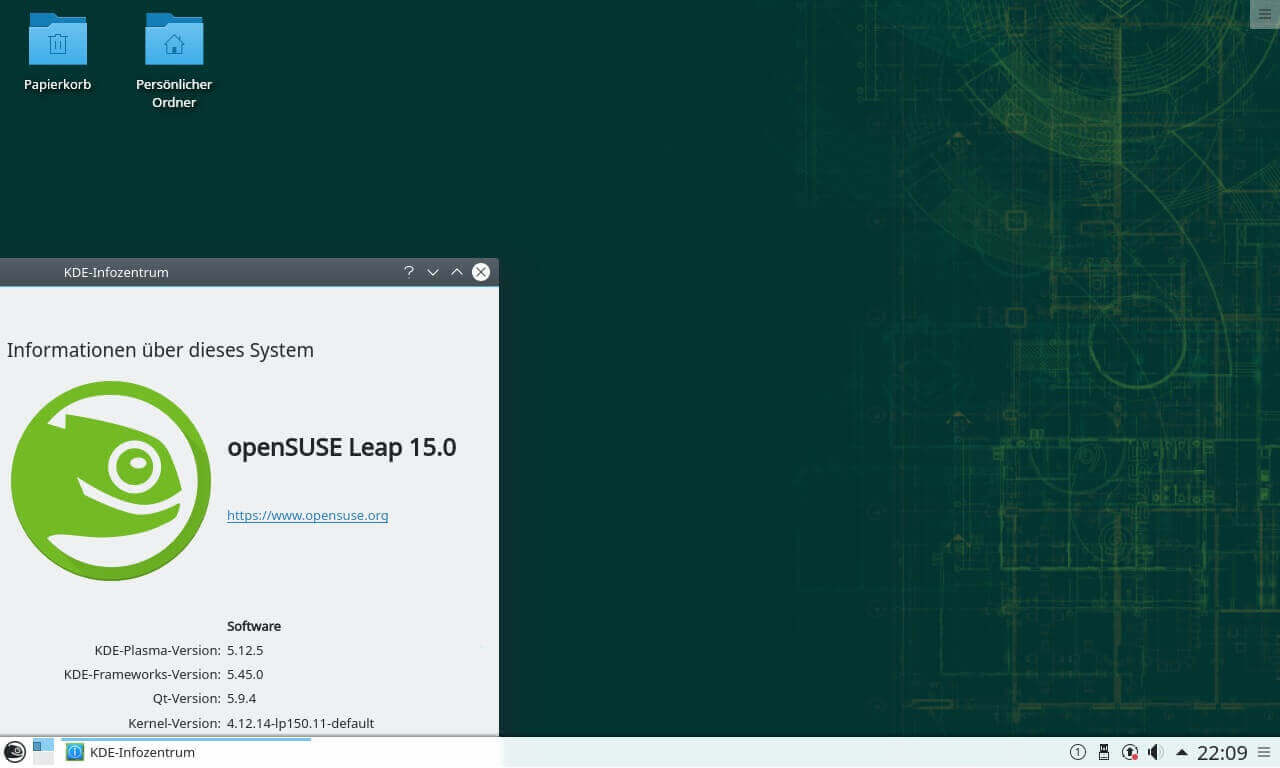
OpenSUSE also provides a plethora of applications out of the box such as office tools, multimedia applications, browsers, and games to mention a few which are used for learners as they learn the ropes.
That was a breakdown of some of the ideal Linux distributions for learners that could potentially help them get started out with Linux without the complexity of setting everything else from the ground up.
They are built to provide a user-friendly UI and a smooth user experience coupled with a bunch of preinstalled applications that simplify the learning path for learners or beginners. As such, if you are looking for an ideal Linux distro for your learning institution, any of these can come in handy.

Anadolu Panteri EDU GNU/Linux much more for student. More than those.