For one reason or the other, you may wish to run a command repeatedly for several times in Linux. This guide will discuss some of the common and effective ways to achieve just that. Let’s consider the first method.
Note that if you intend to run a command after command after every x seconds, you can check out – How to Run or Repeat a Linux Command Every X Seconds
Run a Command Multiple Times in Linux using a Bash for Loop
The easiest way to repeat a command on the Bash shell is to run it in for a loop. You can use the following syntax, where a counter is a variable (you can give it a name of your choices such as i or x etc.) and n is a positive number to represent the number of times you want the command to run:
for counter in {1..n}; do yourCommand_here; done
Here is an example:
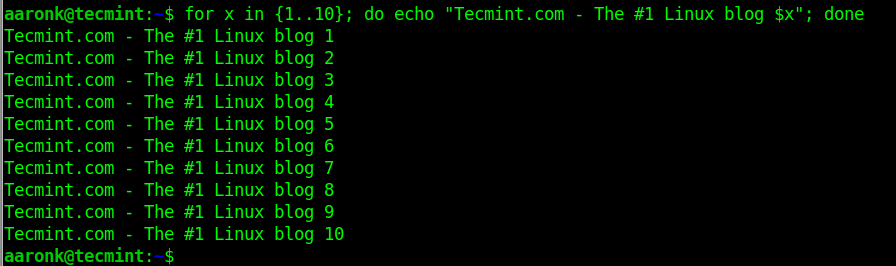
$ for x in {1..10}; do echo "Tecmint.com - The #1 Linux blog $x"; done
Run a Command Multiple Times in Linux using a while Loop
Related to the previous method, a while loop can also be used to run a command many times in Linux using the following syntax:
$ i=1; while [ $i -le n ]; do yourCommand_here; i=$(($i++)); done OR $ i=1; while [ $i -le n ]; do yourCommand_here; ((i++)); done
In the above format, i represents the counter variable, [ $i -le n ] is the test condition and n is the number of times you wish to run the command (ideally the number of times the shell will iterate through the loop.
Another important part of the while loop is i=$(($i+1)) or (($i++)) which increments the counter until the test condition becomes false.
So you can run your command many times like this (replace 10 with the number of times you wish to repeat the command):
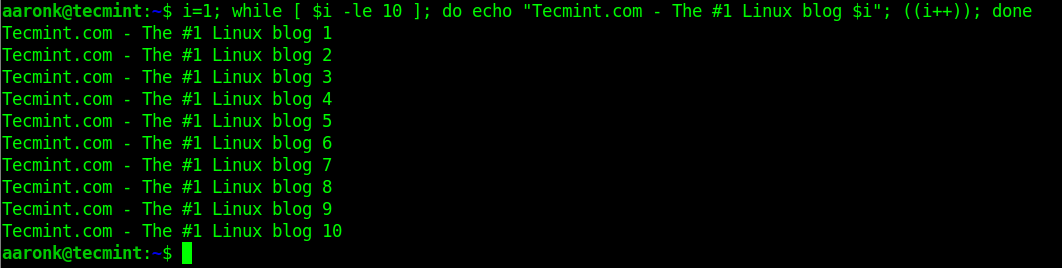
$ i=1; while [ $i -le 10 ]; do echo "Tecmint.com - The #1 Linux blog $i";((i++)); done
Run a Command Multiple Times Using seq Command
The third means of running a command several times in Linux is by using the seq command which prints a sequence of numbers incrementally in conjunction with the xargs command in this form:
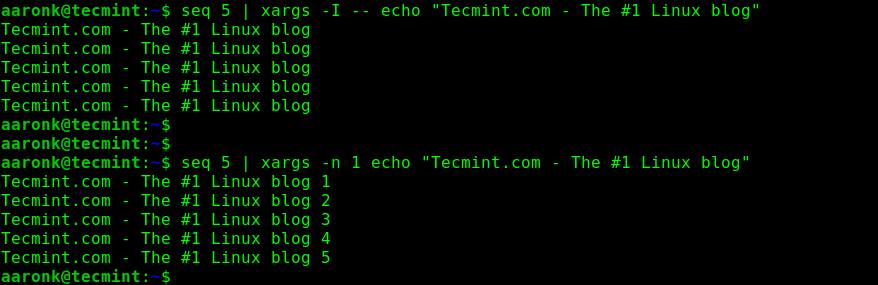
$ seq 5 | xargs -I -- echo "Tecmint.com - The #1 Linux blog"
To add the count at the end of each command, use this syntax:
$ seq 5 | xargs -n 1 echo "Tecmint.com - The #1 Linux blog"
Also, check these related articles:
- 4 Useful Tools to Run Commands on Multiple Linux Servers
- 4 Ways to Watch or Monitor Log Files in Real-Time
- MultiTail – Monitor Multiple Files Simultaneously in a Single Linux Terminal
That’s all for now. If you know of other methods for running a command multiple times in Linux, let us know in the comments section below.