Have you ever been into a situation where you need to search for a string, word or pattern inside a file? if yes, then the grep utility comes handy in such situation.
grep is a command line utility for searching plain-text data for lines which matching a regular expression. If you will divide the word grep like g/re/p then the meaning of grep is (globally search a regular expression and print) which search pattern from the file and print the line on the screen i.e. standard output.
Suggested Read: 12 Basic Practical Examples of Linux grep Command
In this article I will be going to explain advanced commands on grep for the Character Classes in Linux and Unix like operating system.
Here I have considered tecmint.txt is the base file where we will search pattern with the help of grep command in this article for explanation.
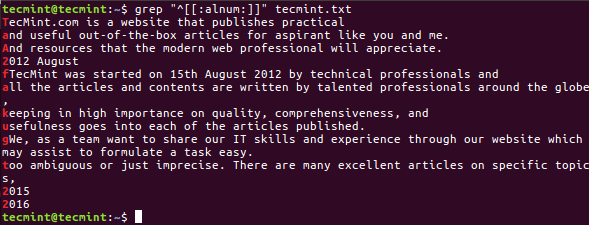
1. Search Alphanumeric Characters
If you have thousands of lines in a file and wanted to search a line which will start from only A-Z, a-z & 0-9 (Alphanumeric Characters).
$ grep "^[[:alnum:]]" tecmint.txt
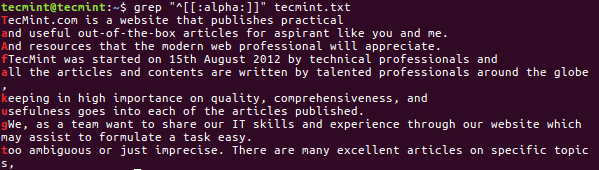
2. Search Alpha Characters
Similar options like if you want to search line which will start from only [A-Z & a-z] i.e. Alpha Characters.
$ grep "^[[:alpha:]]" tecmint.txt
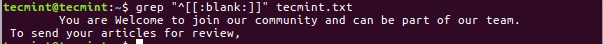
3. Search Blank Characters
Another options like if you want to search line which will start from [Tab & Space] i.e. Blank Characters.
$ grep "^[[:blank:]]" tecmint.txt
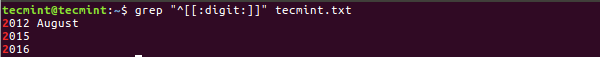
4. Search Digit Characters
The digit option for grep is also very useful to search line which will start from digit [0-9] i.e. Digit Characters.
$ grep "^[[:digit:]]" tecmint.txt
5. Search Lower Letters
Another option for grep is to search line which will start from lower letters i.e [a-z] (Lower Letters).
$ grep "^[[:lower:]]" tecmint.txt
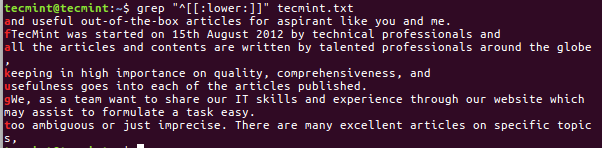
6. Search Punctuation Characters
The Punctuation characters for grep is to search line which will start from [! ” # $ % & ‘ ( ) * + , – . / : ; < = > ? @ [ \ ] ^ _ ` { | } ~. ] i.e. Punctuation Characters.
$ grep "^[[:punct:]]" tecmint.txt
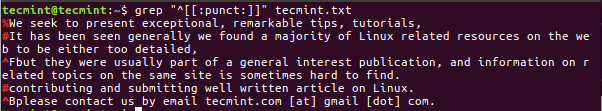
7. Search Graphical Characters
The grep is also used to search a line which will start from Alphanumeric & Punctuation Characters called as Graphical Characters.
$ grep "^[[:graph:]]" tecmint.txt
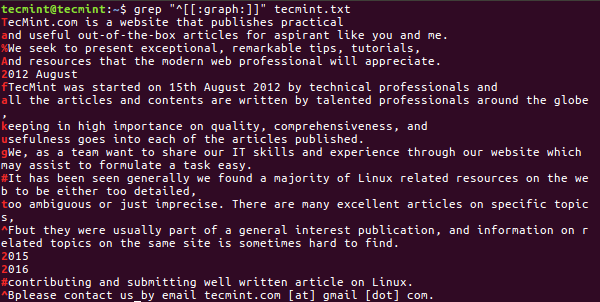
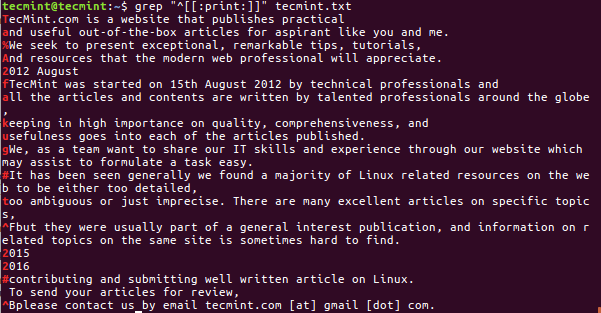
8. Search Printable Characters
Similarly like Graphical Characters, grep is useful to search a line which will start from Alphanumeric, Punctuation and space characters.
$ grep "^[[:print:]]" tecmint.txt
9. Search Space Characters
The grep has also a functionality to search a line which will start from [tab, newline, vertical tab, form feed, carriage return, and space] i.e. Space Characters.
$ grep "^[[:space:]]" tecmint.txt
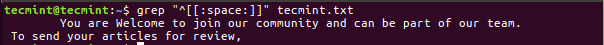
10. Search Uppercase Letters
Another option in the grep is also used to search a line which will start from [A-Z] i.e Upper-case Letters.
$ grep "^[[:upper:]]" tecmint.txt

11. Search Hexadecimal Digits
The grep searches a line which will start from [0-9, A-F and a-f] i.e Hexadecimal Digits.
$ grep "^[[:xdigit:]]" tecmint.txt
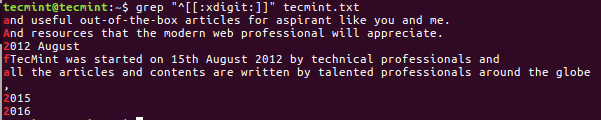
I have explained the advanced functionality of grep which is very strong and powerful tool to search the pattern in a File. Grep is also an important tool for shell scripting and programmers to search the pattern in the programs. It is worth to be familiar with other options and syntax to save the time.
Suggested Read: What’s Difference Between Grep, Egrep and Fgrep in Linux?
In case any issues on the commands which is explained in the article, you can post your comment in the comment section below.




Those aren’t 11 commands – it’s just one “command”. And on your Google Plus post, you showed the “command” ^C which isn’t even explained here…
grep "^[[:punct:]]" tecmint.txtfor Search Punctuation Characters is not working then I tried togrep -c“(” it works but didn’t solve my problemWhen doing search with xdigit it should be within range 0-9 and A-F and a-f only.
@Jonas,
Thanks for pointing out, yes it should be 0-9, A-F and a-f only when using with xdigit.