In this guide, we shall bring to light a simple yet important concept in process handling in a Linux system, which is how to completely detach a process from its controlling terminal.
When a Linux process is associated with a terminal, two problems might occur:
- Your controlling terminal is filled with so much output data and error/diagnostic messages.
- In the event that the terminal is closed, the process together with its child processes will be terminated.
To deal with these two issues, you need to totally detach a process from a controlling terminal. Before we actually move to solve the problem, let us briefly cover how to run processes in the background in Linux.
Table of Contents
Run Linux Command or Process in Background
If a process is already in execution, such as the tar command example below, simply press Ctrl+Z to stop it then enter the command bg to continue with its execution in the background as a job.
You can view all your background jobs by typing jobs. However, its stdin, stdout, and stderr are still joined to the terminal.
$ tar -czf home.tar.gz . $ bg $ jobs

You can as well run a Linux process in the background using the ampersand, & sign.
$ tar -czf home.tar.gz . & $ jobs

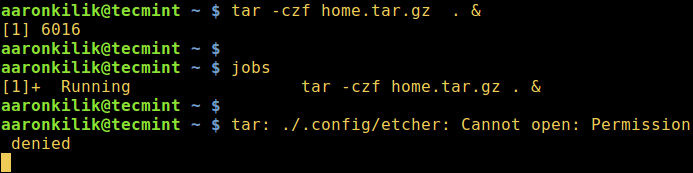
Take a look at the example below, although the tar command was started as a background job, an error message was still sent to the terminal meaning the process is still connected to the controlling terminal.
$ tar -czf home.tar.gz . & $ jobs tar: ./.config/etcher: Cannot open: Permission denied
Keep Linux Process Running After Logout
We will use the disown command, which is used after the process has been executed and put in the background, its work is to remove a shell job from the shell’s active list jobs, therefore you will not use fg, bg commands on that particular job anymore.
In addition, when you close the controlling terminal or log out, the job will not hang or send a SIGHUP to any child jobs.
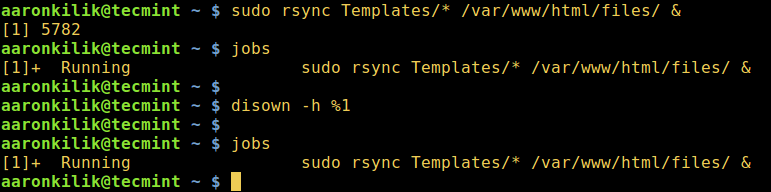
Let’s take a look at the below example of using the diswon bash built-in function.
$ sudo rsync Templates/* /var/www/html/files/ & $ jobs $ disown -h %1 $ jobs
You can also use the nohup command, which also enables a process to continue running in the background when a user exits a shell.
$ nohup tar -czf iso.tar.gz Templates/* & $ jobs

Detach a Linux Process From Terminal
Therefore, to completely detach a process from a controlling terminal, use the command format below, this is more effective for graphical user interface (GUI) applications such as Firefox:
$ firefox </dev/null &>/dev/null &
In Linux, /dev/null is a special device file that writes off (gets rid of) all data written to it, in the command above, input is read from, and output is sent to /dev/null.
As a concluding remark, provided a process is connected to a controlling terminal, as a user, you will see several output lines of the process data as well as error messages on your terminal. Again, when you close the controlling terminal, your process and child processes will be terminated.
Importantly, for any questions or remarks on the subject, reach us by using the comment form below.




Hey, Thanks for this little Linux tip, useful for me to make my Linux commands run in the background…
A slight improvement:
Without the “disown” you’ll get the following output in the source terminal after the given program is closed:
“[1]+ Done firefox /dev/null”
This only happens the next time something is put out to the terminal’s output stream. So, the next time command runs that writes to the output stream.
To test this, run it without “disown”, close firefox, and then run “ls”.
I see this is an old post but I think my question is sort of in the ballpark. what I would like to do is open the console of the process that was started with systemd with a no GUI flag. what this pertains to the Minecraft server.
so I made a systemd service file and the execution command is “java -jar server.jar nogui” now once the system is up and running, I would like to open the GUI or console of the Minecraft server to issue commands without having to open a Minecraft launcher like you would play the game. I know I have done something like this in the past on other platforms but I just don’t know enough about Minecraft/java to make this happen.
I am using ubuntu 18.04 and the current version of the Minecraft is 1.15.2
How to see the jobs running in the previous session? I have submitted jobs in nohup and logged out. After logging again if i wanna see the jobs and if I wanna kill, how to do so
@Bala
You can run this command:
ps -fu username#replace username with your real usernameOR
ps -xOr you can do something simple like:
Exit the terminal or ssh session and it’ll keep running
@B
Great, thanks for sharing this.
Hi,
I am running a script that copy files from one server to 3 other servers. The output I get is warning from other servers when make ssh even when I run the script with & on the end or if I move it in background with
^Zand bg. So my question is can you please give me some advice how can I prevent that output from showing. Thank You in advance.Regards,
Vladimir Todorov
@Vladimir
Good question here. The problem may not be running the script in the background. Have you tried debugging the script:https://www.tecmint.com/enable-shell-debug-mode-linux/; or try to run SSH with the debugging option, as explained here: https://www.tecmint.com/enable-debugging-mode-in-ssh/. This should help you diagnose the cause of the errors. Thanks.
This was very useful! Thank you very much.
I always used 2, 3 terminals to run different apps like android studio, ract-native, node, webstorm, etc. at the same time.
These commands helped me to just have one terminal with all of these running in the background.